We take a top-down approach to review and build security architectures, starting with an understanding of your business goals, IT requirements and current overall architecture. This allows us to map to required security controls and technologies like zero trust, software-defined, virtualization and multicloud.
Our goal is a target security architecture and a roadmap to get there that’s approved by all stakeholders.
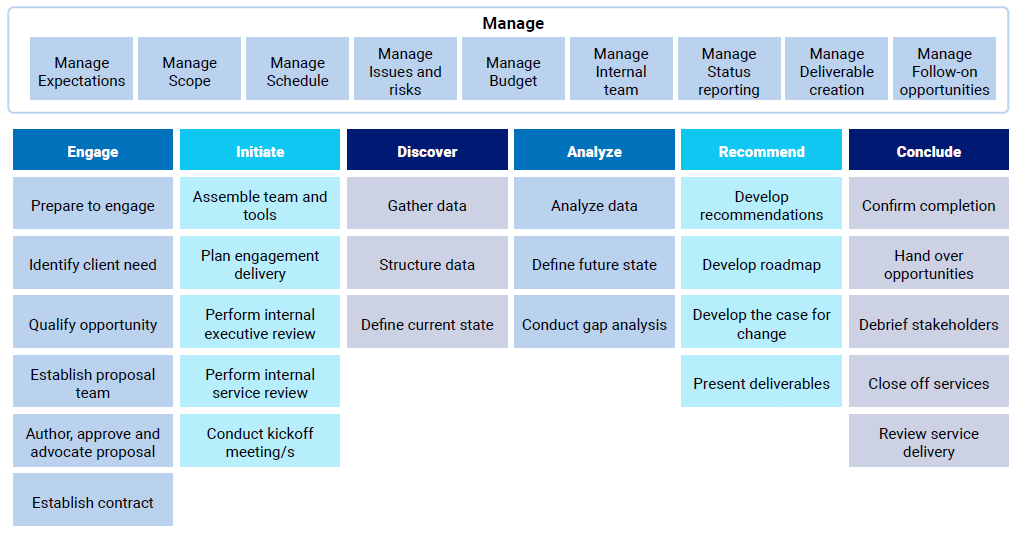
Red dart consulting services lifecycle